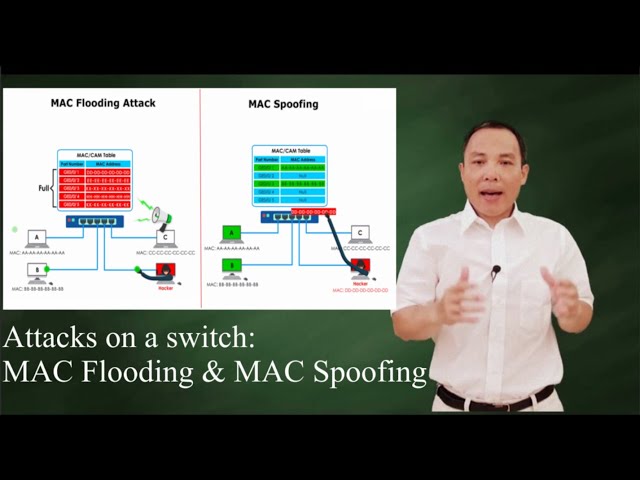
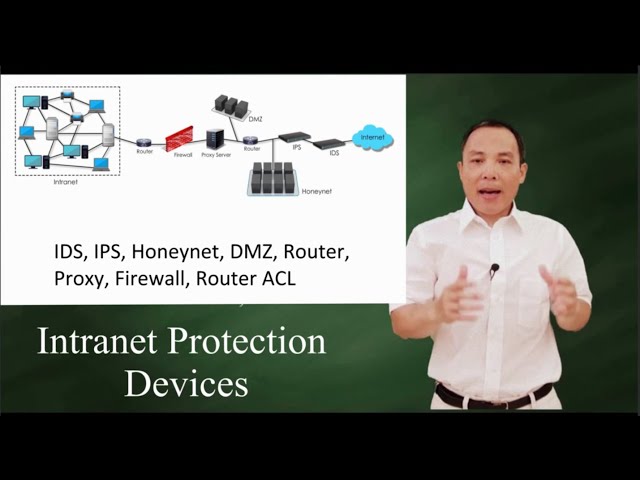
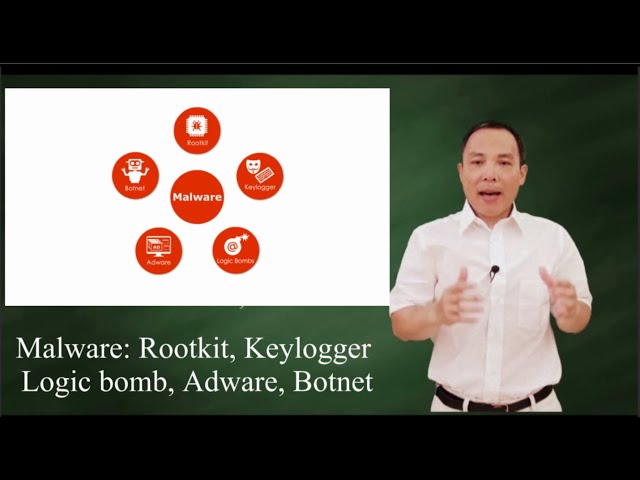
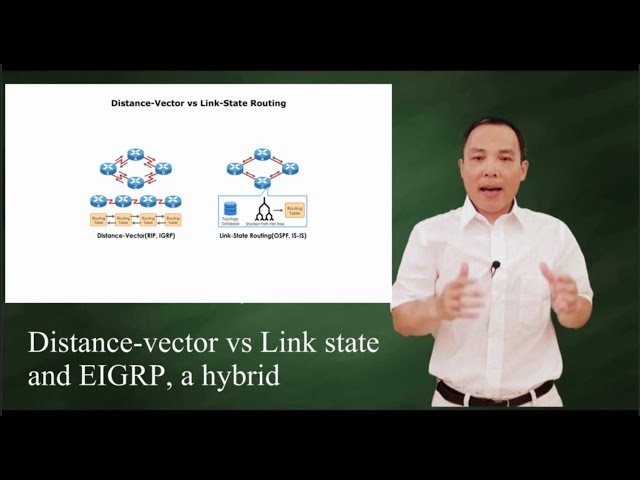
Show more
Sort by
Newest
Oldest
Popular
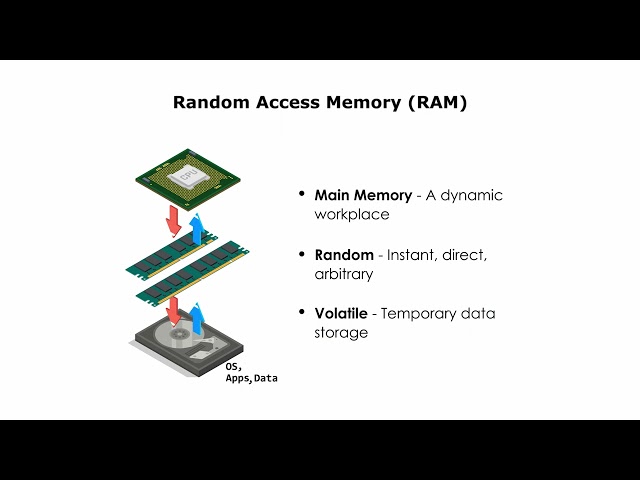
Random Access Memory(RAM)
984 views

Stack and Queue
947 views
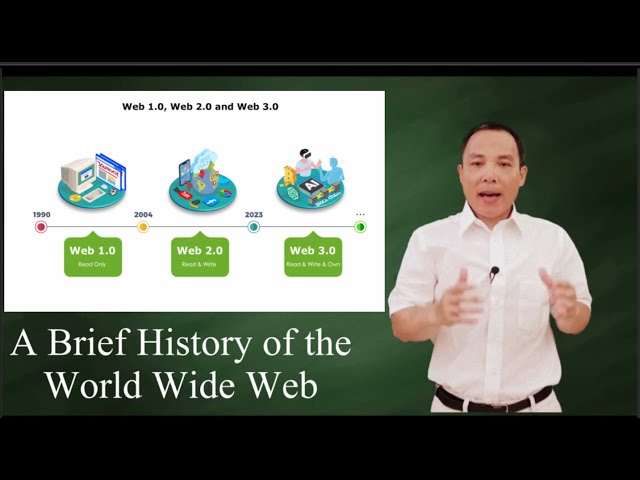
A Brief History of the WEB
1,694 views

How does cellular network work?
11,509 views
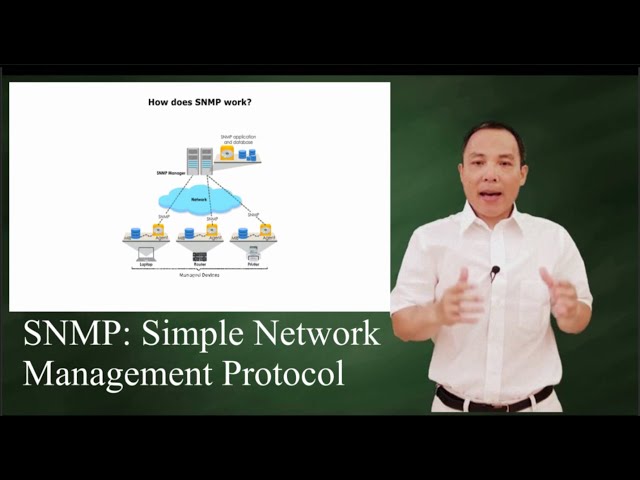
How does SNMP work?
10,183 views

General switch vs managed switch
5,388 views
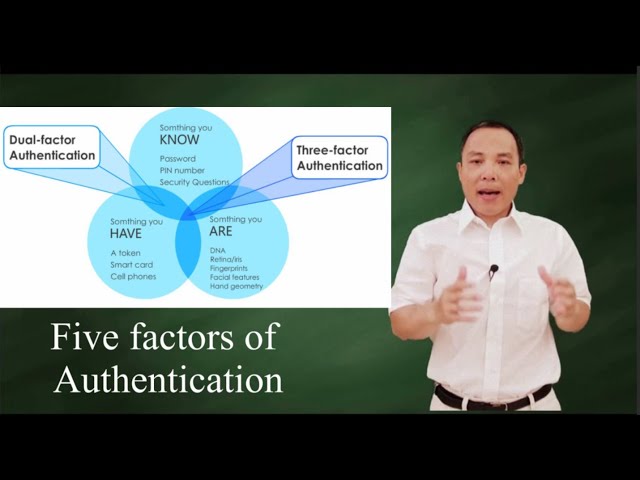
Five factors of Authentication
4,015 views

ChatGPT: A mind-blowing AI
7,026 views
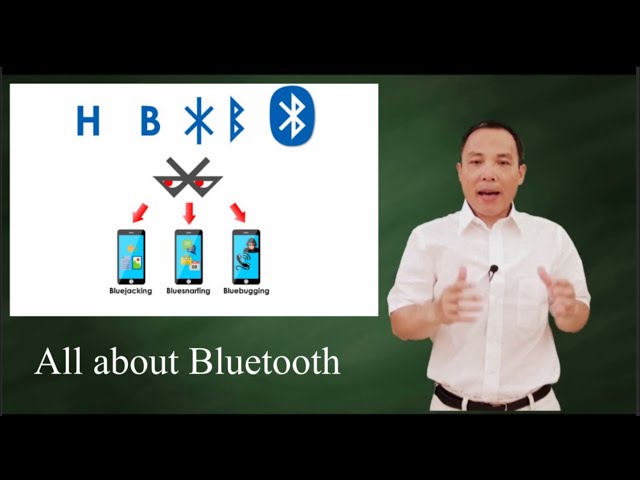
All about Bluetooth
5,410 views
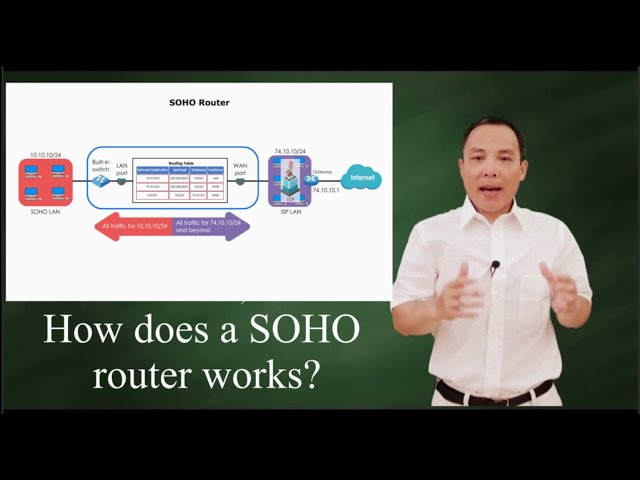
How does a SOHO router works
8,607 views

13 types of computer networks
6,105 views

Data Storage Types: File, Block, & Object
28,766 views
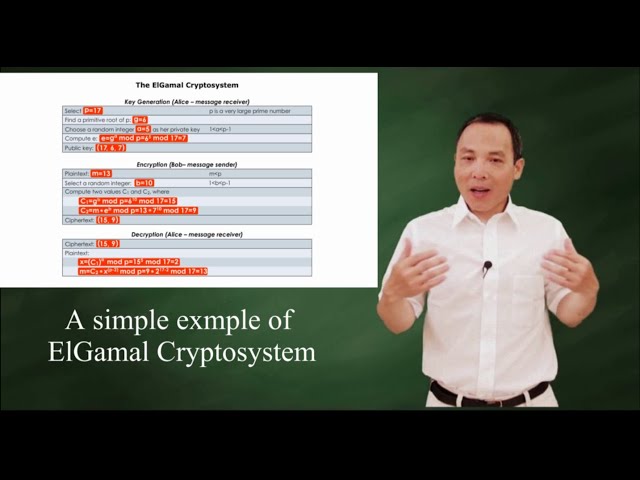
The ElGamal Algorithm: a simple example
8,009 views
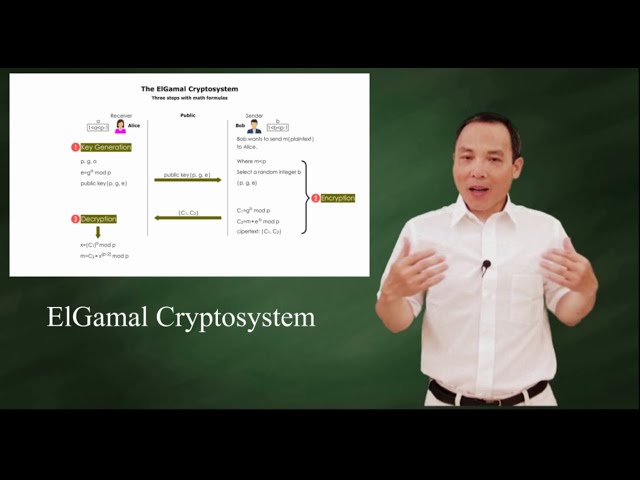
Intro to the ElGamal Cryptosystem
9,594 views