Show more
Sort by
Newest
Oldest
Popular
Hackers Abuse Zero-Day Exploit for CrushFTP
54,964 views

This File Steals Passwords
84,973 views

Hackers Use Github For Malware
62,381 views

Finding WEIRD Devices on the Public Internet
151,018 views
Bypassing SmartScreen on Web Browsers
56,029 views

Telegram Has Been Hacked
193,607 views

Scraping Dark Web Sites with Python
115,525 views

The Apex Legends Hacker: Destroyer2009
112,471 views

Github Copilot Made My Code More Vulnerable
54,224 views
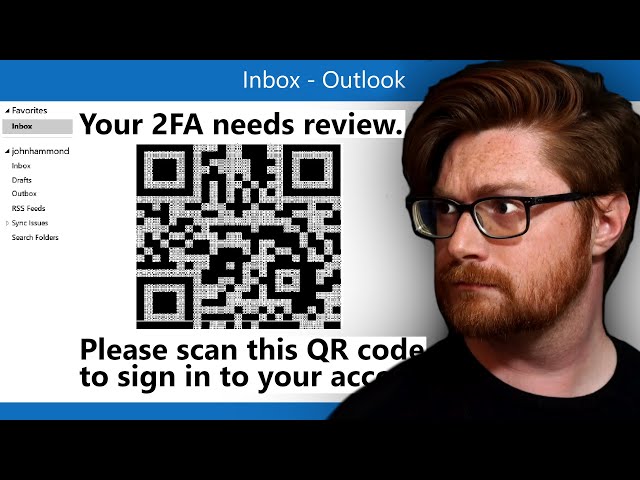
Hackers Can Phish with PLAINTEXT QR Codes
61,557 views

The Apex Legends Hack.
113,064 views
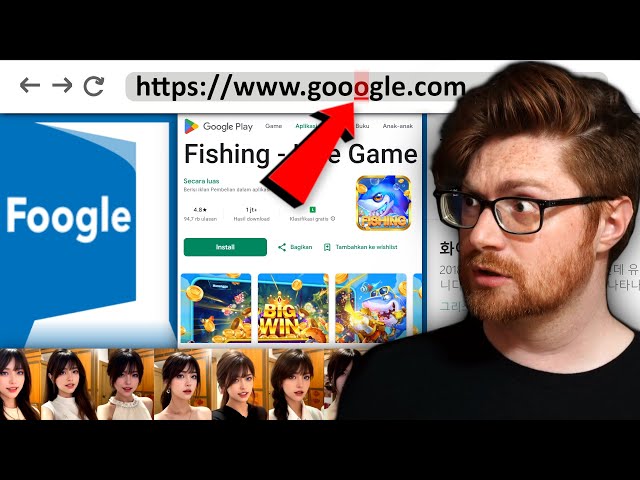
Finding WEIRD Typosquatting Websites
238,916 views

Don't Use CyberChef. Use This Instead.
62,017 views

The Secrets of The Tor Browser
73,974 views

Can a PDF File be Malware?
78,061 views

I Made Malware In Under 20 Minutes
60,645 views
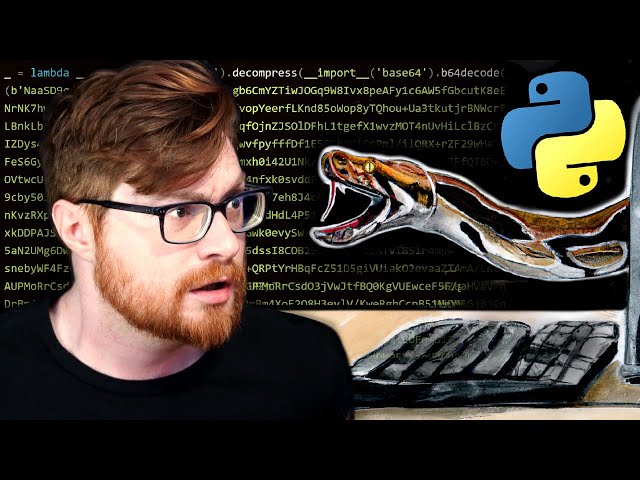
Free Coding Tool Distributes Malware
126,191 views
Sweet New Threat Intel Just Dropped
53,592 views

One Code Mistake Ruined This Website
44,787 views
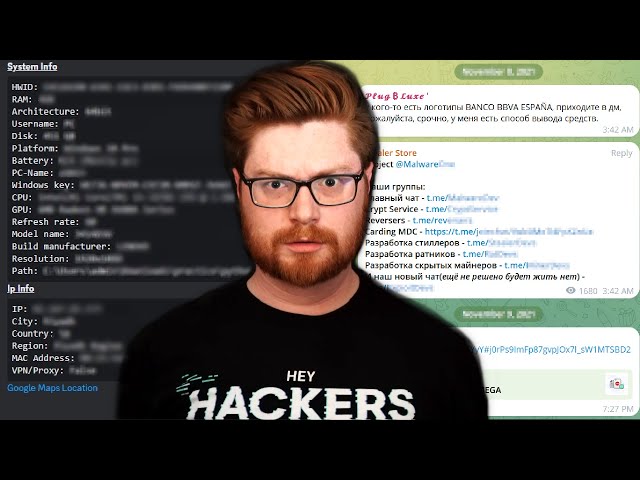
Tracking Cybercrime on Telegram
211,753 views

Don't Forget This One Hacking Trick
57,126 views